End-to-end Device Lifecycle Management
IoT | IIoT | Embedded Devices | Smart Devices | Connected Devices | Gateways | Sensors | Edge Devices
Device lifecycle management in a connected world
Connected devices are already part of society’s critical infrastructure. From automotive, aviation, and defense to energy, smart buildings, and healthcare — devices are becoming smarter, more intelligent, and even autonomous. Whatever its purpose, each device has both hardware and software which require continuous management throughout its life.
To continue innovation and stay competitive, organizations must ensure security and robustness at every phase of the device’s lifecycle.
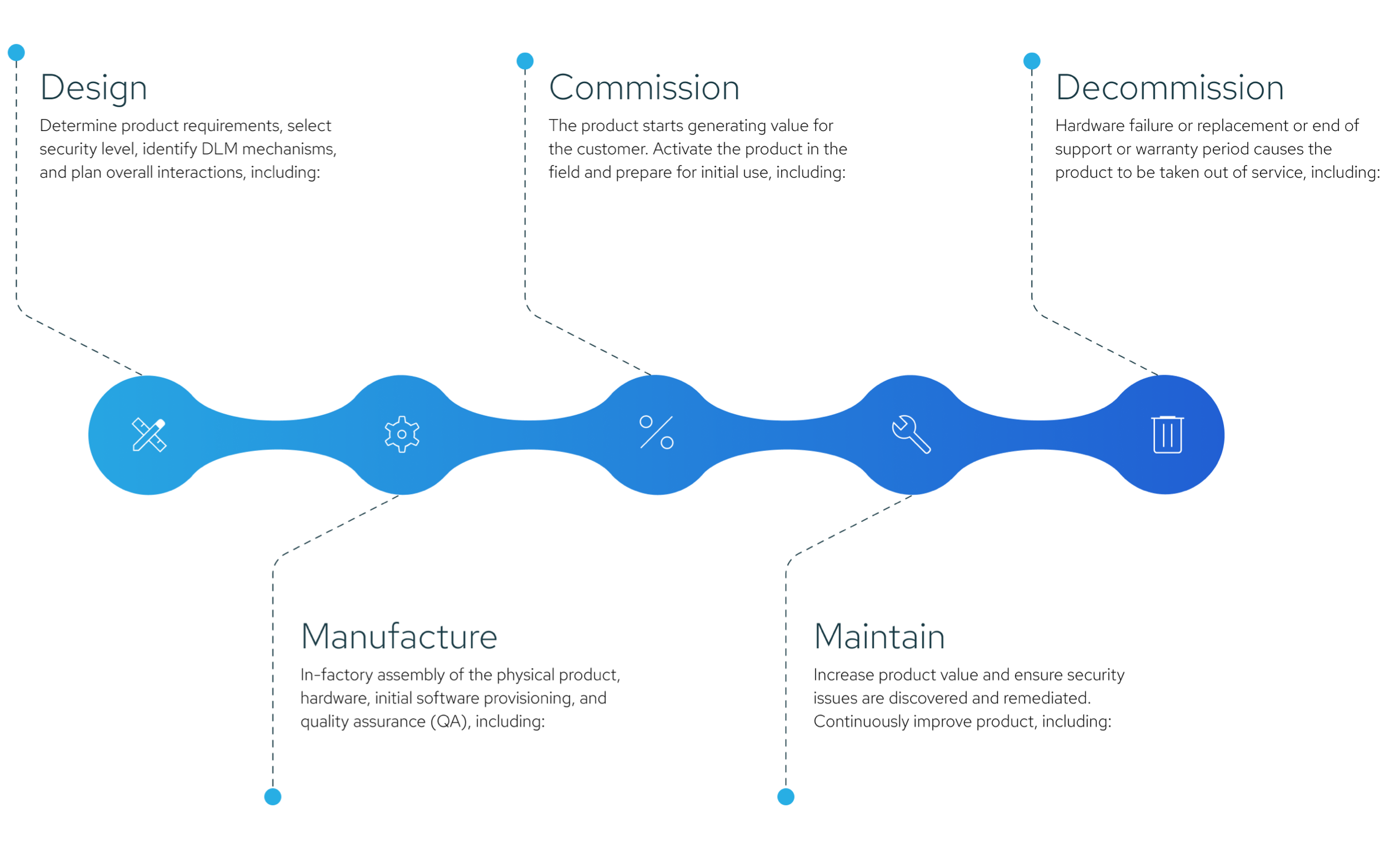
Manage your devices with confidence — in every stage, at any scale
Product release delays, product rework and retooling, quality control issues, security risks, inferior customer experiences — overcoming the challenges around device lifecycle management starts with knowledge. Best practices in device lifecycle management ensures companies deliver the best quality product, with the safest security standards, as efficiently as possible.
Outcomes





From design to decommission
Across the stages of a device, there are six critical elements to ensure superior device lifecycle management that drives business results.
Over-the-air (OTA) updates
Continuously improve product post-release by delivering new software to connected devices in a robust, secure, and scalable way.
Vulnerability management
Secure against avoidable attacks and brand damage by detecting and remediating new software vulnerabilities as they become known - on a continuous basis.
Secure boot, software integrity and chain of trust
Protect against malware, taking control of foundational components of the device and verifying software signatures during the booth process.
Storage encryption and IP protection
Defend against industrial espionage, avoid competitors copying your solutions, while safeguarding the company brand from adverse publicity on data privacy.
Credentials management and public key infrastructure (PKI)
Limit the impact of compromised access credentials by ensuring uniqueness and adhering to the principle of least privilege. Manage credential revocation during a security incident or decommissioning to avoid future exploitation.
Source of truth
To control and secure, all connected devices must be defined in one, central place where lifecycle stage and other key DLM information, like connectivity status, installed software version, and owner, are maintained. A source of trust also serves as the point for synchronization to other systems, like ERP.
A partner you can trust
We have worked with hundreds of companies, helping them transform into the most efficient and secure device producer in their industries. With Northern.tech as your trusted partner, produce faster with confidence and compete better in the market.
Tailored evaluation
Our most experienced DLM experts come on-site and evaluate your environment.
Technical training
We train you in the best practices, ideal processes, and overall architecture.
Analysis and report
Receive an extensive report of gaps and recommendations for your environment.
Industry rating
Get your DLM rating scored against your industry peers, highlighting current strengths and weaknesses.
Ecosystem access
Gain access to a network of trusted partners for further guidance or requirements.
See how your process scores
It's difficult to objectively judge the state of your own device lifecycle management. Chat to one of our experts about an evaluation.
